Between March and June 2025, cybersecurity firm Proofpoint reported a series of coordinated spear-phishing campaigns by Chinese hacking groups aimed at Taiwan’s semiconductor industry. The attackers, targeted both corporate and financial entities across the supply chain.
The phishing methods were tailored to specific roles inside organizations. Emails imitating job applicants, investors, and legal professionals were used to deliver malware or harvest credentials.
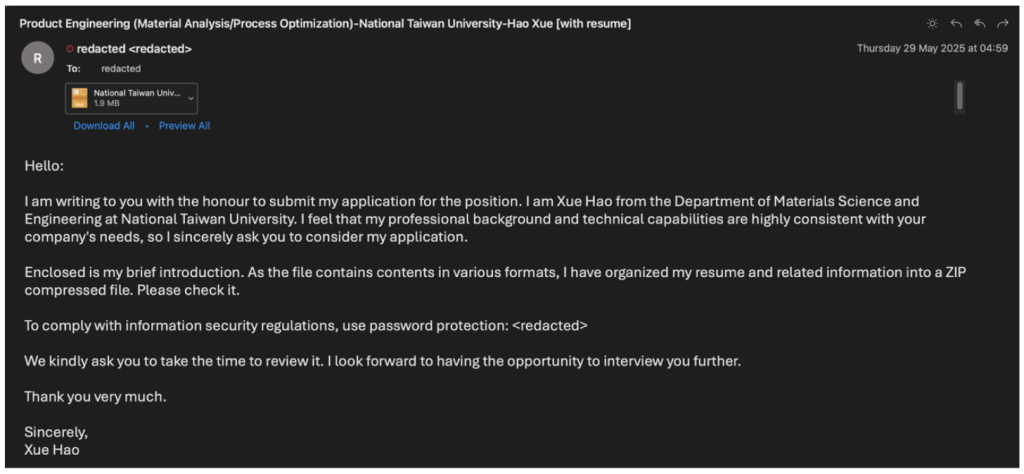
One of the identified actors, tracked as UNK_FistBump, used email accounts compromised from Taiwanese universities. These were employed to send fake job applications to HR departments. The emails included malicious attachments disguised as resumes—either in PDF form or ZIP archives hosted on external services like Zendesk or Filemail. Once opened, they delivered malware such as Cobalt Strike or a backdoor referred to by Proofpoint as “Voldemort.”
An example cited in Proofpoint’s analysis featured the subject line: “產品工程(材料分析/製程優化)-台灣大學-薛豪 [附履歷]” (translated: “Product Engineering (Material Analysis/Process Optimization) – National Taiwan University – Xue Hao [with resume]”).
Another cluster, named UNK_DropPitch, focused on financial analysts covering semiconductor firms. These emails impersonated representatives from investment firms and included ZIP files containing DLL payloads. The goal was to install remote access tools such as a malware family dubbed “HealthKick.”
UNK_SparkyCarp employed credential phishing through adversary-in-the-middle (AiTM) kits. Messages appeared to be account security alerts and directed recipients to phishing sites like “accshieldportal.com,” designed to intercept login credentials.
A fourth group, UNK_ColtCentury—also known as TAG-100 or Storm-2077—sent benign legal inquiries to build trust. Later emails in the same threads included links or files that deployed SparkRAT, a remote access Trojan.
Proofpoint noted that 15 to 20 organizations were affected, mainly smaller companies with less robust cybersecurity infrastructure. Although larger manufacturers such as TSMC, MediaTek, UMC, Nanya, and RealTek may have been in the threat actors’ scope, no public reports confirm breaches of these firms.
The report highlights how spear-phishing remains a core tactic in cyber-espionage operations. These efforts align with China’s ongoing strategy to reduce dependence on foreign semiconductor technology and gain access to sensitive industry data.
Proofpoint’s full report can be accessed here.




